Keeping on Top of Certificate Expiry
Certificates are essential for all public-facing websites. They help browsers and users confirm the identity of the domain they're connecting to.
As part of our proactive monitoring approach, it's important to have automated alerts for key infrastructure events — one of those being certificate expiry.
Why we choose AWS Lambda
We’re using AWS Lambda and Slack to handle these alerts because our certificates are managed in AWS. Lambda is cost-effective, scalable, and easy to deploy. Slack is our main communication tool and actively monitored by our team — so it made sense to use that as the alert destination.
How it works
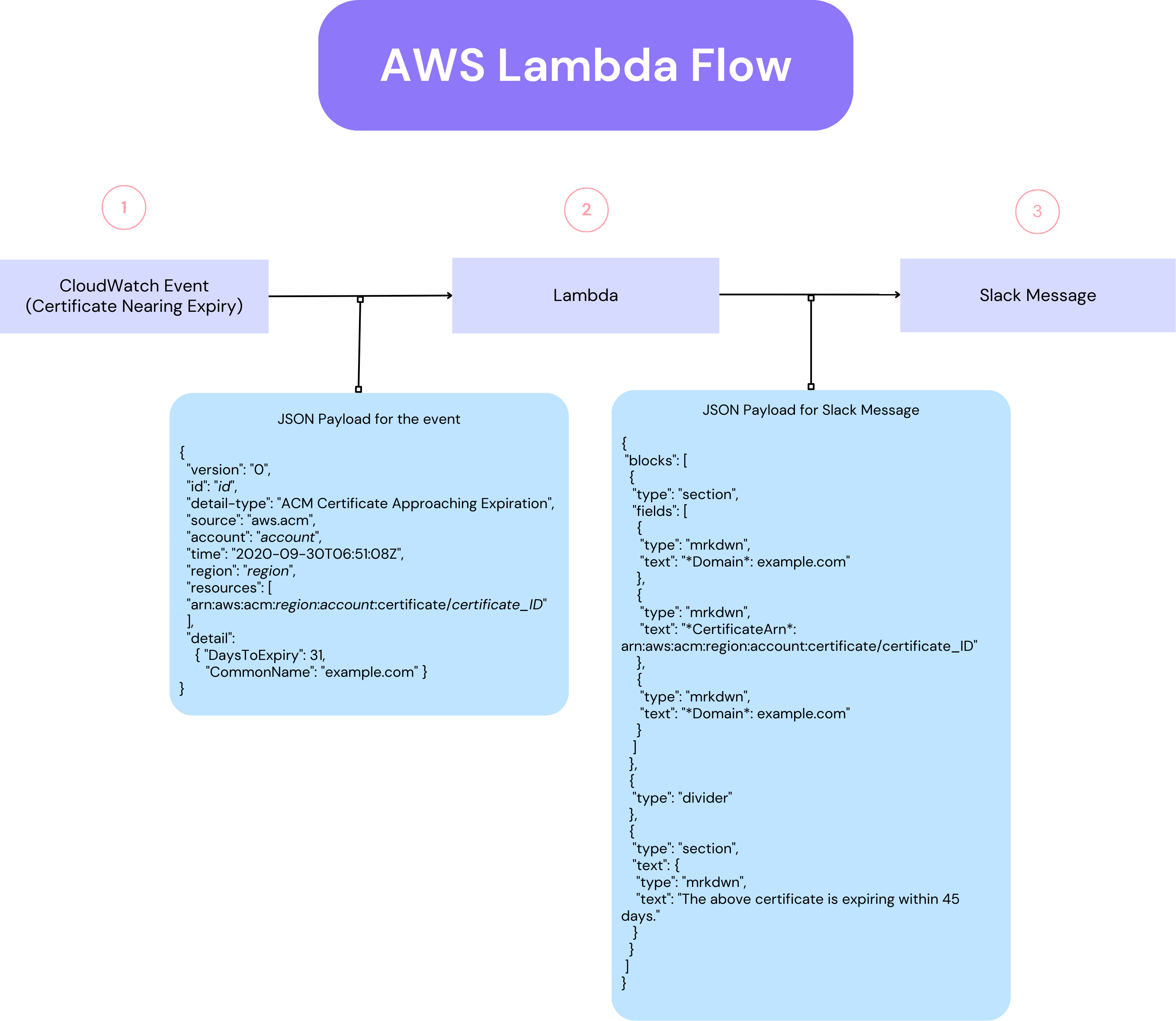
A CloudWatch event triggers the Lambda function when a certificate is close to expiring. The Lambda then checks the event payload for the certificate ARN and posts a message to Slack that includes:
- Domain name
- Certificate ARN
- Expiry date
- A short message
We’ve open sourced this Lambda — you can find it here.
Following is the flowchart explaining how it works:
Setting It Up
Prerequisites
- An AWS account with the right IAM permissions
- AWS CLI installed and configured
- A Slack workspace with an incoming webhook set up
- Basic GoLang knowledge (helpful, but not essential)
Step 1: Create the Lambda Function
- Create an IAM policy like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid":"LambdaCertificateExpiryPolicy1",
"Effect": "Allow",
"Action": "logs:CreateLogGroup",
"Resource": "arn:aws:logs:<AWS-Region>:<AWS-ACCT-NUMBER>:*"
},
{
"Sid":"LambdaCertificateExpiryPolicy2",
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": [
"arn:aws:logs:<AWS-Region>:<AWS-ACCT-NUMBER>:log-group:/aws/lambda/handle-expiring-certificates:*"
]
},
]
}
Create a role for the Lambda:
- Choose Lambda as the service
- Attach the policy from Step 1
- Example name:
lambda-certificate-expiry-function-role
In the AWS Console or CLI:
- Create a new Lambda function
- Select Go as the runtime
- Use the role created above
Upload the
lambda-handler.zipfile from the latest releaseSet the Lambda timeout to 30 seconds
Add the environment variable
SLACK_WEBHOOK_URLwith your Slack webhook URL
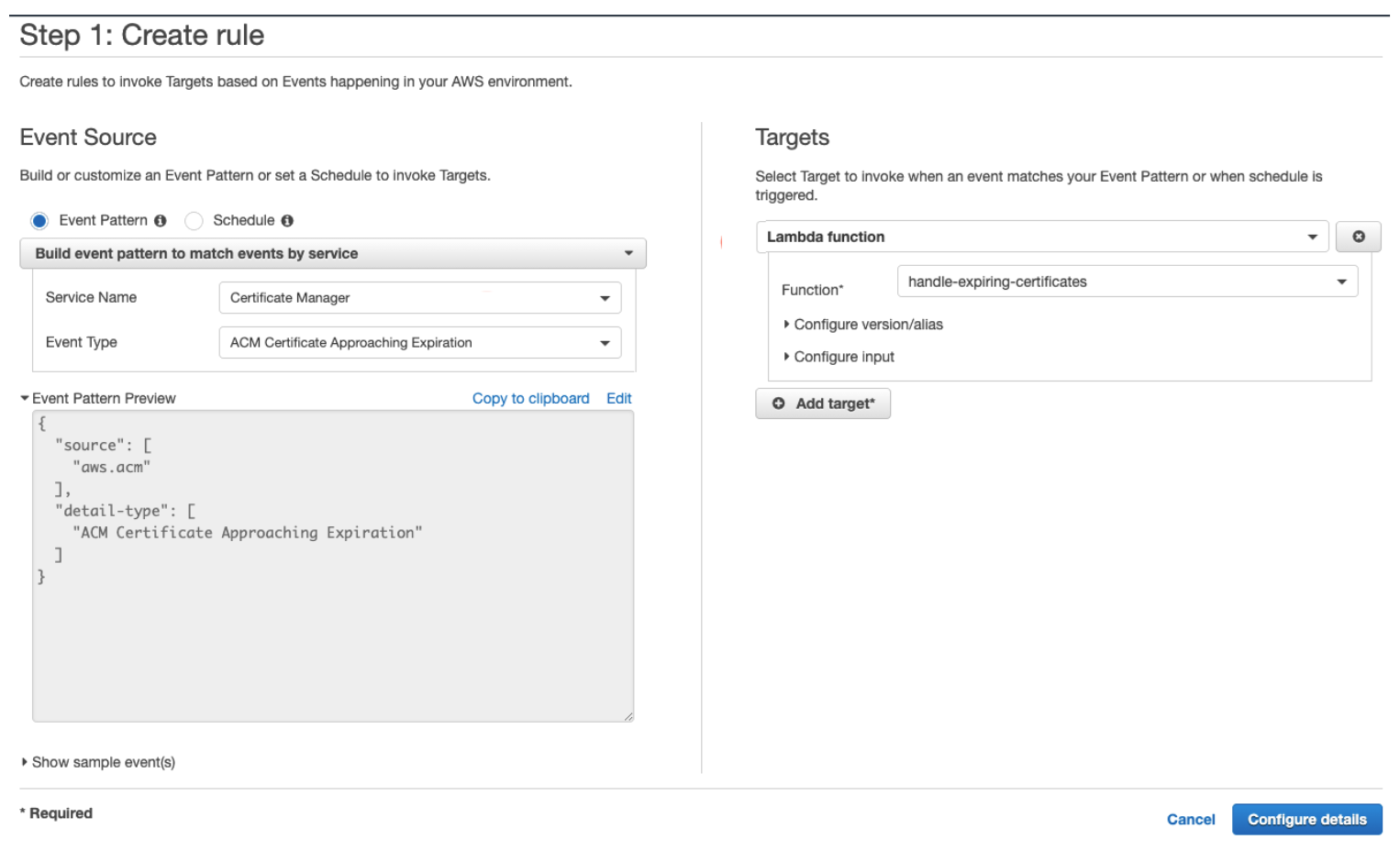
Step 2: Create the CloudWatch Rule
Set up a CloudWatch event to trigger the Lambda when certificates are about to expire. Here's how:
- Follow the AWS guide to create a CloudWatch rule
- Use these settings:
- Service Name: Certificate Manager
- Event Type: ACM Certificate Approaching Expiration
- Target: Your Lambda function
This event fires daily for certificates expiring in 45 days or less. You only need to configure it once — after that, it’ll keep notifying Slack.
Step 3: Test & Monitor
Make sure everything’s working:
- Manually test the Lambda and check if Slack receives the notification
- Use CloudWatch Logs to review Lambda runs and errors
- Confirm notifications include the expected info and arrive on time
Ready to Use
This Lambda is plug-and-play — easy to drop into your workflow and already maintained with updates to the AWS API.
Want to contribute or suggest improvements? Open an issue or submit a pull request.